- Vmware Send Ctrl Alt Del
- Vmware Horizon Ctrl Alt Del Macbook
- Vmware Horizon Ctrl Alt Del Mac Remote Desktop
- Esxi Ctrl Alt Del
- Ctrl Alt Del Windows 10
When I was still working as an Escalation Engineer for VMware® Global Support, there was a time-honored tradition among the Broomfield center's EUC support group: If you left your computer unlocked and walked out of eyesight, you'd always come back to a surprise. The HR folks would probably be unhappy at such an unauthorized use, but a quick flip of the screen with Ctrl-Alt-Up and a dash back to your desk, leaving their display inverted and the surrounding engineers glancing over for the inevitable reaction, was worth the risk.
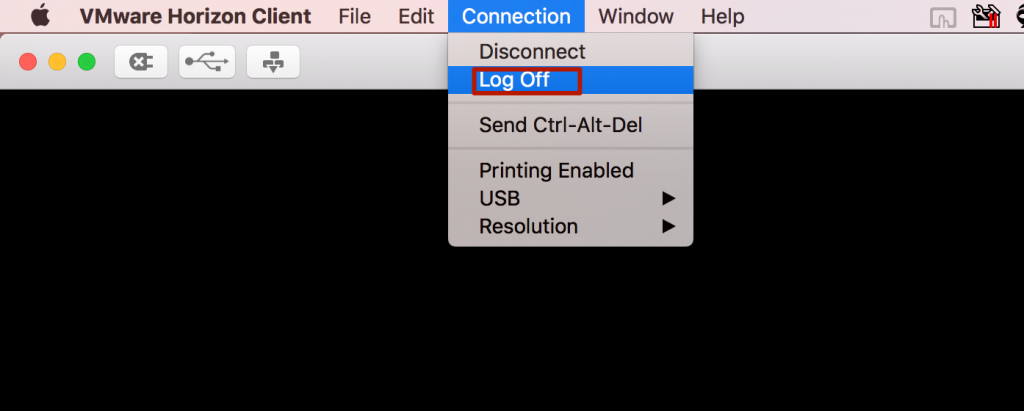
Mwb1100 writes: 'Use Ctrl-Alt-End in the RDP client to send a Ctrl-Alt-delete to the remote session.' Thanks for the tip mwb1100. Your approach sends a Ctrl-Alt-Del to the remote host which triggers the Windows Security screen and the following dialog from Player.
- Ctrl-P Edit preferences. Ctrl-Alt-Enter Go to full screen mode. Ctrl-Alt Return to normal (windowed) mode. Ctrl-Alt-Tab Switch among open virtual machines while mouse and keyboard input are grabbed. Ctrl-Tab Switch among open virtual machines while mouse and keyboard input are not grabbed. VMware Workstation must be the active application.
- Under the 'VMware Horizon Client for Mac' click the 'Go to Downloads' button. On the download page, browse to the bottom and click on the 'Download' button. When the download is complete, click on the Downloads button. Double click on the 'VMware-Horizon-View-Client' download.
All the 'fun' of fixing your machine when you got back to your desk could have been prevented by hitting those three little keys we all know: Ctrl-Alt-Del. A quick press and the system is secured from any would be mischief-doers, and a smart Technical Support Engineer remembers this when he gets up from his desk in VMware GSS. We all do, or should, secure our system as a good habit when we step away, but when you're running a virtual machine, it can have an unintended consequence: the VDI session can also receive this keystroke and act on it.
A colleague recently came to me with a question from his customer: Is it possible to script it so that VMware Horizon® Client for Windows would behave similarly to the Linux client when handling Ctrl-Alt-Del and Windows-L? That's a loaded gun ready to fire, for those in security call this something: malware—bypassing the kernel is a big taboo. Of course, there are those thinking, 'Mike, this is easy, just use the PCoIP Session Variables to block the keystroke!' And you'd be right, with PCoIP, but few actually sit down and ask the simple question familiar to childhood, 'But . . . why?'
Secure Attention Key (SAK)
First, for some context, let's take a little trip down the rabbit hole of operating-system design. In all modern operating systems, there is something called the Secure Attention Key (SAK), which can be invoked by the user. It is an old concept originating in the early 1990s, when stealing someone's password wasn't typically a malicious act, rather a display of your prowess. By simply showing you could, it was known that your skills with the infrastructure of the day were sound. The forward thinkers of the world concluded that a user should definitively know that the screen they were about to enter credentials into was that of a trusted security subroutine and not a fake.
Almost a funny notion these days of ever-increasing security, but from it we were left a legacy in the familiar keystrokes we still use to get into our operating systems. It varies between operating systems, but the principles of operation are the same, be it Windows or Linux. Now, there are endless debates on the usefulness of the SAK and whether it truly increases security in the modern era, but, for our purposes, the story of its origins is important to answering my colleague's question because the SAK defined the keystrokes we use today.
In that proverbial Paleolithic period of IT that is now the NT days (my, how far we have come), the engineers sat down to find a keystroke that could be used by the security subsystem, too. After much discussion, it turned out that one single keystroke wasn't in use for another purpose within the operating system itself: Ctrl-Alt-Del. Before that, Ctrl-Alt-Del had humbly succeeded its predecessor Ctrl-Alt-Esc on the original IBM PC keyboard. It was an excellent combination, insofar as it would save the clumsier (or angrier) of us from accidentally (intentionally) bumping (slamming a fist into) the Ctrl-Alt-Esc and rebooting the machine leading to (more) frustration. So, Ctrl-Alt-Del was enshrined within Windows NT 3.1 as the Secure Attention Key, a proud tradition that we carry on in the 21st century.
Horizon Client Behavior on Linux and Windows
With that history and humor in mind, let's look at the answer to my colleague's question from two different Horizon Client–side operating systems: Linux and Windows, specifically what happens on those systems in context with the behavior of the Horizon client.
Linux has two attributes that are very important, and put a quick end to the issue of Ctrl-Alt-Del:
- The SAK keystroke is usually Break-K or Ctrl-Alt-Pause.
- The somewhat cliché adage, 'Everything is a File.'
That combination makes for a very easy workaround which you can find in the following document at the bottom of page 39: https://www.vmware.com/pdf/horizon-view/horizon-client-linux-document.pdf Simple, effective, and also leaves more options on the table. There are a lot of flavors of Linux, and it can be customized to do basically anything you'd like, but in general, the more popular flavors have designed Ctrl-Alt-Del to bring up a Task Manager.
Windows is a bit different. In your standard Windows Client to Windows VDI scenario, the Secure Attention Key is the same on both ends. In Windows, when the Secure Attention Key is invoked, there are different actions invoked by the kernel; we are only concerned with the happenings after a user is logged in, which is the invocation of Windows Security. From its humble origins, it has evolved into the familiar screen with options to lock, sign out, change your password, call up the task manager, and (in the XP successors) switch users. Importantly, Windows-L also invokes the Windows Security process, but to directly lock the system rather than present the familiar menu.
The important takeaway is that when this key is pressed, only one thing in the computer has the authority to intercept it: the kernel. There are, of course, ways to subvert the kernel and intercept the keystroke, but for malicious software that has made it to that point, intercepting a user's password is inconsequential since, for all intents and purposes, it is the system at that point.
And so it is we return to my Technical Support Engineer from above. When he locked his machine with the intention of ensuring he didn't return to a Justin Bieber background, he forgot that this was going to lock his VDI session as well. In the grand scheme of the universe, this is a minor inconvenience, but in our modern age of ultra-low latency systems that can render a 4K display at 60+ FPS and serve up the world at your fingertips, most end-users find it to be a near capital offense on the part of both the computer as well as the VDI Administrator that put it in front of them.
The Mighty Keystrokes
In closing, if you're using PCoIP, setting the PCoIP session variables to block Ctrl-Alt-Del is a simple thing, and the PCoIP engine will dutifully ignore the input and not relay it to the VDI OS's kernel. Otherwise, it comes down to user training to click through the appropriate invocation of Lock via the Start menu of the version of Windows they are running. It won't hurt to let them know they aren't alone, and even we at VMware occasionally run afoul of the all-powerful Windows Security and its mighty keystrokes.
How to Connect to Desktops Using the Browser
Click here to open a new webpage to desktops.ualr.edu
Macos catalina which macs. Click 'VMware Horizon HTML Access'
Make Sure that on the drop-down menu, student is selected.
Type in your student domain credentials and the password you set for it. They will be the first part of your UA Little Rock e-mail address.
Click login, here you should see two connections, CSTEM Student and ITS Student Lab. ALWAYS use CSTEM Student. ITS Student Lab is not guaranteed to save your information. Once you click on CSTEM Student, you will be taken to the desktop and will have access to available programs.
How to Download and Use the VMware Horizon Client
Click here to open a new webpage to desktops.ualr.edu
Click 'Install VMware Horizon Client'
This will take you to VMware's download page. From here you should locate your operating system (Windows, Mac OS, Chrome OS, etc.) and then click the corresponding 'Go to Downloads' button.
Once you've clicked the 'Go to Downloads' button, you might be faced with multiple choices of a download. Download the first one you see.
After the download finishes, double click on the file you just downloaded and you should be met with this screen:
Click 'Agree & Install' and the program will do the rest. Your computer might prompt you to allow this program to install, click yes.
After it installs, you will need to restart your computer. Once you have restarted your computer, you should see the VMware Horizon Client shortcut on your desktop. Click on this shortcut to open the program.
When you open the program you will see this screen that shows your server connections. Double click this to view your available connections. Use xbox one controller on mac. Remember, ALWAYS use CSTEM Student. If you use ITS Student Lab, your information is not guaranteed to be saved properly on this connection.
When you double click the connection server, you will be prompted to enter your credentials (the first part of your email and the password you set for the student domain).
After you login, you will be able to connect to the CSTEM Students VM.
How to Use the Tool Bar in Desktop Mode
When using your desktop in a browser, there is a tool bar on the left hand side. You can access this by clicking on the small ribbon.
This tool bar shows the different connections that are available to you as well as provides a few functions for importing files, copying and pasting, sending the ctrl-alt-del command, and a menu list for logging out and a few other tasks.
Here are examples of the different tasks available through this tool bar.
Sending a CTRL + ALT + DEL CommandTransferring Files to and from the Virtual EnvironmentCopying and Pasting Between the Virtual Environment and Your OSMenu List for Logging out and Other TasksHow to Add a Computer to UA Little Rock's Wired Network by Mac Address
Click here to open a new webpage to access.ualr.edu.
Log in using your Net ID and the password you set for it.
Once logged in, you will see your registered devices. From here you can also register new devices, manage them, or log out.
To add a new device, click 'Add new device'.
You will be taken to a page where you can enter the devices Mac address and name the device. Once finished, agree to the terms and click 'Create'.
Once added, you will see the summary of your device. Your device is now authenticated.
Click 'View active sessions' to view authenticated devices that are active now.
Click 'Manage existing devices'.
This is where you can edit, delete, or disable devices that you have authenticated.
How to Allow a Computer to Authenticate on UA Little Rock's Wired Network
Click the Start button and type 'Services.msc'.
In the services window, find the service titled 'Wired AutoConfig'.
Right click on 'Wired AutoConfig' and click 'Properties'.
Select 'Automatic' from the drop-down next to 'Startup Type' and click OK then Apply.
Restart your computer.
Right click on the network icon in the lower right hand corner of your screen. Click on 'Open Network and Internet Settings.'
From there, Click on 'Network and Sharing Center.'
Vmware Send Ctrl Alt Del
Click on the blue text next to 'Connections' and then select properties.
Click on the Authentication tab and make sure that IEEE 802.1X authentication is enabled and that the authentication method is Microsoft:Protected EAP (PEAP).
Click settings next to network authentication method and make sure to uncheck 'Verify the server's identity by validating the certificate' and click OK.
Click 'Additional Settings' and select 'Specify authentication mode'. Select 'User authentication' then click 'Save credentials'. A window will pop up prompting you for a username and password. Enter your Net ID for the Wifi and the associated password. Exit out of everything and unplug your computer from the Ethernet and plug it back in. You are now able to use UA Little Rock's wired network!
How to Connect to UA Little Rock's WiFi on a Chromebook
Vmware Horizon Ctrl Alt Del Macbook
If you are logging in for the first time on your Chromebook, skip to step 4.
Click on the WiFi symbol in the bottom right corner.
Click on 'No Network'
Click on 'UALR-WiFi' you will be taken to this screen:
Make sure that next to 'EAP Method', 'PEAP' is selected from the drop-down menu.
For Identity and Password, put in your Net ID and its associated password. Make sure 'Save Identity and Password' is checked so that you don't have to log in every time you leave the network.
Click 'Connect' and you should be connected to UA Little Rock's WiFi network! If you experience issues with authentication, please make sure that your Net ID and password are correct before contacting CSTEM IT.
How to Use Google Drive with UA Little Rock's VMware System
Sign in to your UA Little Rock Gmail account.
Look at the top right of the screen. You should see 9 squares that form a bigger square. Click on this. (If you do not see these squares, simply google 'Google Drive' in your browser).
Click on the 'Drive' icon and it will take you to this screen.
Click 'New' and you will see options to create a new document or to upload documents from your computer. If you open Google Drive in VMware, it will upload files from the VM.
Vmware Horizon Ctrl Alt Del Mac Remote Desktop
You are also able to drag and drop files from a desktop or folder directly into the browser to upload them to Google Drive.
Once a file or folder is dragged into Google Drive, you can access and download these files anywhere as long as you log into your UA Little Rock e-mail address to access Google Drive.
How to Print to the CSTEM Lab's Printer from VMware
Esxi Ctrl Alt Del
NOTE: Before reading this, be aware that the CSTEM Lab printer will ONLY print from the Thin Clients located in the lab. You cannot print from personal computers.Log in to VMware
Open up Word or another application you can print from.
If you do not see the 'CSTEM-Lab-Printer' option, close Word or your printing application and go to your desktop.
Double click on the 'UEM User Environment Refresh' icon on the desktop.
After this, wait a few minutes and then open up Word or a printing application again. Follow steps 1 and 2 again to see if you have the printer.
Ctrl Alt Del Windows 10
If you still do not see the printer, close out everything again and double click the 'UEM User Environment Refresh' icon again.
After this, click on the start menu and type 'Control Panel' click on the option that says 'Control Panel'
Click on 'View Devices and Printers' under the 'Hardware and Sound' heading.
If you see an object under 'Unspecified' you should now have access to the CSTEM-Lab printer. If you do not see this, please continue refreshing until you do see it. Once it is there, you are able to print!
